How to Access Blocked Websites Securely
We have all been subjected to countless internet restrictions and limitations. While there can be legitimate reasons to ban websites, it can eventually lead to over-restriction. That’s when the resistance kicks in, encouraging us to look for ways to use blocked websites.
Here, we have compiled several methods that will help you carry out ISP (Internet service provider) unblock without breaking a sweat!
With these strategies employed by ISPs to block websites, the questions of how the user can use blocked websites emerge. Let’s read on how to access the blocked websites securely.
8 Easy Methods to Access Blocked Websites
With these strategies employed by ISPs to block websites, the questions of how the user can use blocked websites emerge.
If an ISP shuts down a website and it is no longer accessible online, archived snapshots can still be examined by doing a date-wise search. This process, of course, can only be used as a short-term or one-time treatment.
There are various techniques to get over ISP blocking, and we’ll go over the most effective ones below
- DNS Resolver - To avoid DNS blocking, one can always use a DNS resolver. Certain websites can frequently be unavailable in the browser. A DNS works by turning online links into IP addresses and providing access to them; but, if in case the ISP has blacklisted a specific IP address, its DNS will not allow access to it.
- VPN - In this instance, a VPN is the most trusted solution because it will fix the majority of problems. We feel that having a VPN is crucial for maximum internet security, regardless of whether the user is facing ISP blocking. It is critical to select an effective VPN, and there is no better option than SPL VPN.
- Proxy - A proxy server is similar to a VPN. It conceals the user’s original IP address and routes requests to the appropriate domains.
- Tor - The Tor network is free and easy to use. It is possible to connect to the network by installing the Tor browser and selecting a connection. While some countries prohibit Tor, the service essentially circumvents restrictions by enabling Tor to utilize its network throughout.
- Alternate URLs and Mirror Sites - If the ISP restricts access to a website, access can be restored to it by using its official and unauthorized mirror sites and alternate URLs, if they are accessible. Currently, all major websites have mirror sites to assist the user if the site is blocked.
- Short URLs - This approach is both simple and effective: simply copy and paste the URL of a restricted website into an online URL shortening service. See the magic happen!
- HTTPS method - This approach will not work with all websites, but it is still worth a shot. To switch to HTTPS, do the following: Open the browser and replace the ‘http: //’ section of the address with ‘https: //’ or put ‘https: //’ before the ‘www.’ part. This can help the user use blocked websites.
- Wayback Machine - We saved the most basic method for last. Any data shared on the Internet is never forgotten. The Wayback Machine is one of the best examples of such memories being saved. Almost every online page gets cached, with at least one snapshot kept in the Wayback Machine. Many more are freely available as this is the single largest online archive.
That’s where modifying the DNS resolver comes into play. It operates such that when a user connects to a resolver of their choice, the ISP’s DNS resolver gets bypassed. It will help use blocked websites that would not be accessible otherwise.
This one-click VPN and its 1000+ servers give users the privacy and protection they need to use blocked websites. If a user is experiencing IP blockage, SPL VPN generates a new IP address for the user as soon as they connect to a server.
We feel that a VPN is the option to go with when deciding whether to use a DNS resolver or a VPN because of its various functions—a VPN not only offers the user access to prohibited content but also adds an extra layer of security and hides internet browsing activity.
The issue is that proxies do not offer the same level of encryption as VPNs, which means the user will be vulnerable to DPI and DNS filtering. On the other hand, lower encryption provides faster browsing performance. However, avoid utilizing free proxies because they are widely used and utilize bandwidth - which significantly slows down the performance.
Tor protects user privacy by utilizing its onion routing, in which traffic data is encrypted and routed through many intermediary nodes. While Tor may be slightly slower, it is a resilient technology that will always put the user one step ahead of any attempts at censorship or limitation.
Read more on the differences between Tor and VPN
Tor does come with several disadvantages. The Tor browser will frequently disable media plug-ins that can get abused to divulge personal information to protect user identity. Similarly, it disables scripts automatically, resulting in a slightly less feature-rich surfing experience.
If an ISP shuts down a website and it is no longer accessible online, archived snapshots can still be examined by doing a date-wise search. This process, of course, can only be used as a short-term or one-time treatment.
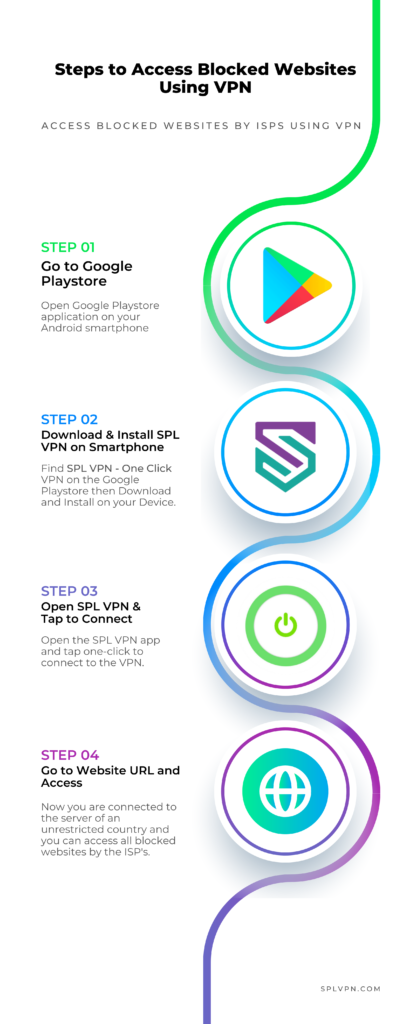
Steps to Access the blocked websites using a VPN
How ISP Block Websites?
The strategies employed to block websites are usually straightforward. A smaller and less complex ISP will block access using simple ways, such as using firewalls that blocks IP addresses of blocked content. Stronger ISPs, on the contrary, ensure that the framework gets integrated and that the user cannot acquire access, which is an excellent reason to conduct some research before choosing an ISP; check to see if the ISP under consideration employs excessive website filtering.
Websites Blocking Methods utilized by ISPs
There are solutions to use blocked websites to counter blocks established by ISPs. However, to do so, one must first determine which approach the ISP employs. ISPs utilize one of the following strategies:
1. Firewalls - Firewalls assist ISPs in defining the kind of content their clients are or are not permitted to view. In essence, your ISP creates rules for inbound and outbound traffic, and the firewall upholds those restrictions. Additionally, all of your connections pass through the network of your ISP. As a result, you have to abide by their set rules.
Firewalls also operate on an IP basis. Your IP address is also given to you by your ISP. Therefore, the firewall traffic rules automatically apply to you when you use it to browse the web.
2. Deep packet Inspection - DPI is a technique for analyzing the network to see data requests. DPI software allows the user to examine the websites they wish to visit and view the page titles. This data enables the service provider to configure firewalls or DNS filters to block the desired material. This is a violation of privacy and internet security since all the content is getting watched over without consent.
3. DNS Filters - Domain Name System works differently than IP blocking; it filters or blocks access to a website by restricting the site’s IP address rather than the users. DNS blocking is simple and easy to circumvent; in most circumstances, it could be the firewall protecting the user from malicious content online.
If the user has reason to assume it is their ISP, this is a typical strategy used by smaller ISPs. Assume the ISP wishes to prohibit Facebook. Instead of returning the original Facebook IP address, the DNS would provide a bogus page that will not work or lead the user to a blank page explaining why they can’t access it when typing the website link in the bar.
Though this page sheds light on how ISP blocks websites and the methods mentioned can help access blocked websites, VPNs remain the perfect solution to this problem. A VPN is a terrific way to access prohibited information and even secure your online privacy, with top companies offering thousands of servers scattered across worldwide networks. Subscribe to SPL VPN today to access 1000+ servers, 100% free of charge. This free Android VPN App offers blocked content with top-notch safety and security.








One Comment